and the distribution of digital products.
The Unseen Threats: How FinTechs Can Safeguard Their Future with Robust Cybersecurity
\ The world of finance is changing, and it’s changing fast. Over the past decade, technology has redefined how people manage their money, make payments, and even invest. What was once a world dominated by traditional banks is now teeming with start-ups and companies offering digital solutions in finance, commonly known as FinTechs. These companies are driving the future of finance with mobile payments, digital wallets, online lending, and cryptocurrencies.
\ But this transformation comes with a significant risk. As FinTechs continue to gain popularity, they also become a prime target for cybercriminals. Protecting financial data, preventing fraud, and ensuring the security of mobile payment systems and crypto wallets have become top priorities. Without strong cybersecurity, FinTechs will face serious threats to their operations and their customers’ trust.
The State of Cybersecurity in FinTech: Numbers Don’t LieThe statistics are alarming. In 2024 alone, the average cost of a data breach in the financial sector was over $6 million. These figures are especially concerning for FinTech firms, which are often more vulnerable due to their reliance on agile technologies and fast-paced development cycles. Most of the breaches reported in the financial sector in recent years have involved FinTech companies, underlining the urgency of securing digital finance systems.
\
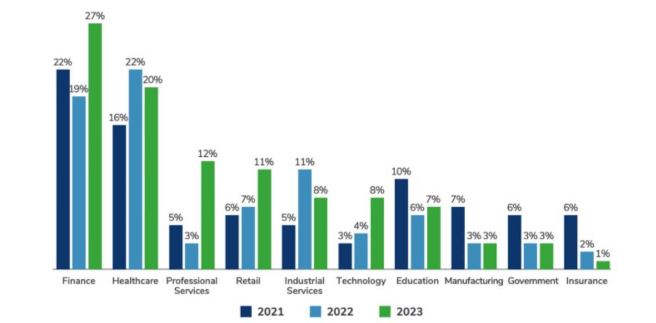
Figure 1: The distribution of data breaches from 2021 to 2023 across different industries.
\ Take a look at some high-profile breaches that occurred in the past few years. For instance, Finastra, a London-based FinTech company, suffered a severe data breach, leading to the theft of approximately 400 gigabytes of compressed data. In 2017, Equifax, a major US-based credit reporting agency, exposed the personal information of nearly 147 million people due to a failure to update their servers with a security patch. That breach cost Equifax roughly $425 million in fines and damages. Similarly, in 2022, Flagstar Bank faced a data breach that compromised the Social Security numbers of 1.5 million customers.
\ Then there’s the growing issue of money laundering. A report from 2023 revealed that a staggering $22 billion was laundered via cryptocurrency platforms alone. Cybercriminals continue to use FinTech applications for illegal activities, making security breaches even more damaging.
\ These figures and examples highlight the magnitude of security risks faced by FinTech applications. As more sensitive data is handled digitally, protecting that data becomes not just a technical challenge but a critical necessity for business survival. FinTech companies need to focus on building products that inspire trust and ensure the safety of their users' financial information.
The Key Cybersecurity Challenges FinTechs FaceOne of the primary challenges for FinTech companies is the sheer volume of sensitive data they handle. Financial institutions, including FinTechs, are a goldmine for cybercriminals because of the personally identifiable information (PII) they store—things like social security numbers, credit card details, and bank account information. With data like this on the line, FinTechs are prime targets for attackers.
\ The scale of the data makes it hard to protect. But it’s not just about the data itself; it’s also about the rapidly changing landscape of cyber threats. Cybercriminals are constantly developing new strategies and technologies to bypass traditional security measures. For instance, identity fraud alone led to $23 billion in losses in 2022, according to a study by Javelin. Other types of fraud, such as phishing scams, credential stuffing, and advanced persistent threats (APTs), are becoming harder to detect and prevent.
\ Another challenge FinTechs face is the ever-present risk of non-compliance with financial regulations. Companies operating in the financial sector must follow strict laws, such as the General Data Protection Regulation (GDPR) in Europe, the Payment Card Industry Data Security Standard (PCI DSS), and anti-money laundering regulations. Failure to comply with these laws can result in hefty penalties, making it even more difficult for FinTechs to maintain business operations.
\ With so many threats and challenges, FinTech companies must take proactive steps to secure their applications and their customers’ data.
Essential Security Measures Every FinTech Needs to Implement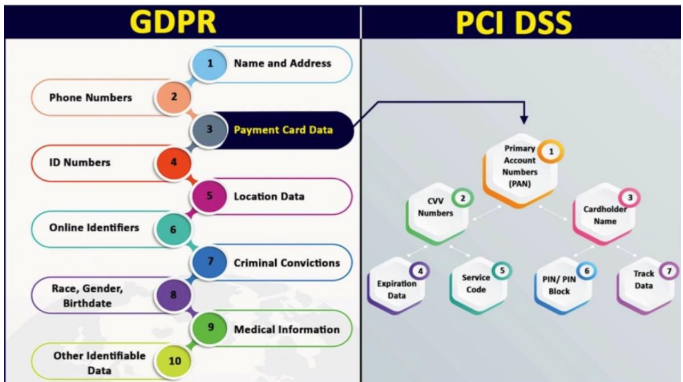
Figure 2: The scope of PCI DSS and GDPR
\ To protect user data and prevent fraud, FinTechs must invest in several key cybersecurity measures. Let’s break them down:
1. Data Encryption: Securing Information at Every StageData encryption is one of the most important steps any FinTech company can take to protect sensitive customer information. Encryption ensures that even if data is intercepted during transmission or access is gained by a malicious actor, the data will be unreadable without the decryption key.
\ If a FinTech company is handling credit card information, it must encrypt the data before storing it. This way, even if hackers break into the system, they won’t be able to access the actual credit card numbers. Implementing strong encryption protocols, like the Advanced Encryption Standard (AES), can protect data effectively.
\ Here's an example of how to implement encryption in Python using the cryptography library:
\
| from cryptography.hazmat.primitives.ciphers import Cipher, algorithms, modesfrom cryptography.hazmat.primitives.kdf.pbkdf2 import PBKDF2HMACfrom cryptography.hazmat.primitives import hashesfrom cryptography.hazmat.backends import defaultbackendimport os# Generate a key (in practice, use a secure key management system)password = b"securepassword" # Use a strong passwordsalt = os.urandom(16) # Generate a random saltkdf = PBKDF2HMAC( algorithm=hashes.SHA256(), length=32, salt=salt, iterations=100000, backend=defaultbackend())key = kdf.derive(password)# Encrypt sensitive data (e.g., a credit card number)def encryptdata(plaintext, key): iv = os.urandom(16) # Initialization vector cipher = Cipher(algorithms.AES(key), modes.CFB(iv), backend=defaultbackend()) encryptor = cipher.encryptor() encrypteddata = iv + encryptor.update(plaintext.encode()) + encryptor.finalize() return encrypteddatasensitivedata = "4111111111111111" # Example credit card numberencrypteddata = encryptdata(sensitivedata, key)print("Encrypted Data:", encrypted_data) | |----|
\ You can also decrypt the data during transactions or audit records by following the coding example below.
\
| def decryptdata(encrypteddata, key): iv = encrypteddata[:16] # Extract the IV cipher = Cipher(algorithms.AES(key), modes.CFB(iv), backend=defaultbackend()) decryptor = cipher.decryptor() decrypteddata = decryptor.update(encrypteddata[16:]) + decryptor.finalize() return decrypteddata.decode()decrypteddata = decryptdata(encrypteddata, key)print("Decrypted Data:", decrypted_data) | |----|
\ Even If the data is breached, the attacker will only see an encrypted data like this below:
\
| Userdata | EncryptedCard_Data | |----|----| | 1 | b’\x8b\xf4…\xaf’ |
\ The key point here is to make sure as a developer, that you use a strong key management system (KMS). I use AWS KMS or HashiCorp Vault in most cases to secure encryption keys for my clients. Also, rotate the keys periodically to enhance the security. Magora Systems, for example, uses HTTPS/TLS to encrypt data during transmission between the client, server, and database, and this is a good approach to ensure the security of data at rest and in transit.
\
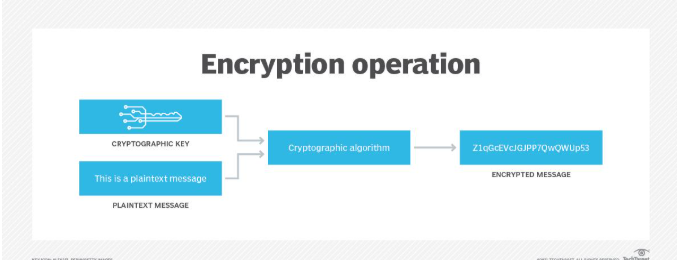
Figure 3: How cryptographic key works in data encryption.
2. Multi-Factor Authentication (MFA): Verifying User IdentityMulti-factor authentication (MFA) is a critical security measure that adds an extra layer of protection. By requiring users to verify their identity with something they have (e.g., a phone), something they know (e.g., a password), and something inherent to them (e.g., biometric data), FinTechs can significantly reduce the risk of unauthorized access to accounts.
\ I often advise developers to leverage open libraries for MFA, such as PyOTP for backend TOTP generation and Google Authenticator for client-side. Even if a hacker steals a user’s password, they would still need the second factor (the OTP) to gain access.
\ Take a look at this example code below to have a grasp of how the backend setup in Python will look like:
\
| from flask import Flask, request, jsonifyimport pyotpapp = Flask(name)userdata = {} # Simulate a [email protected]('/register', methods=['POST'])def register(): user = request.json['username'] secret = pyotp.randombase32() userdata[user] = {"secret": secret, "password": request.json['password']} return jsonify({"message": "Registered successfully!", "secret": secret})@app.route('/login', methods=['POST'])def login(): user = request.json['username'] password = request.json['password'] otp = request.json['otp'] userinfo = userdata.get(user) if not userinfo or userinfo['password'] != password: return jsonify({"message": "Invalid credentials!"}), 401 totp = pyotp.TOTP(userinfo['secret']) if not totp.verify(otp): return jsonify({"message": "Invalid OTP!"}), 401 return jsonify({"message": "Login successful!"})if name == 'main': app.run(debug=True) | |----|
\ On the client side, you can configure the registration so that users can scan a QR code generated from the server's secret key or they can input their password and the TOTP from their authenticator app during login.
\ Below is an example code for that function:
\
| |
|----|
\ With MFA embedded in apps, it becomes more difficult for threat actors to gain access to sensitive systems or individual data.
\ I noticed that this simplified MFA setup through QR codes and familiar tools (authenticator apps) has more user adoption, since most clients I have worked with prefer the model.
\
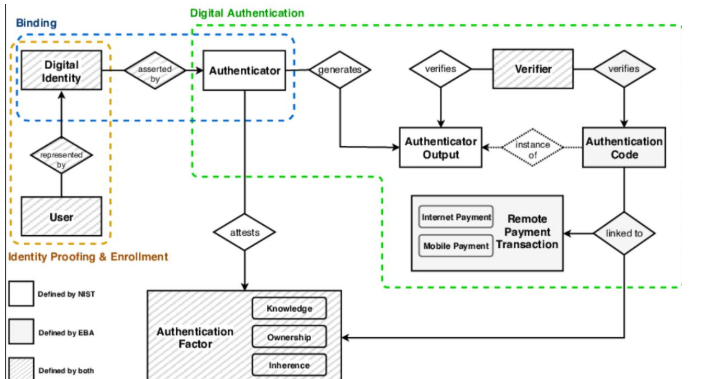
\ Figure 4: MFA Conceptual Model.
3. Data Masking and TokenizationMasking and tokenization are two other variables that I encourage fintech app developers to employ to protect financial data.
\ Data masking works by transforming sensitive data into an obscured or fictionalized version during transactions. Depending on your intent, you can set up static masking or dynamic masking. Both ensure that real data, such as customers' PII remains secure while supporting operational needs.
\ While working on a mobile app that requires credit card info, I will usually mask most of the credit card details so that only the last four digits will show as illustrated in the example code below.
\
| def maskcard(cardnumber): return f"**** **** **** {cardnumber[-4:]}"print(maskcard("1234567812345678")) # Output: **** **** **** 5678 | |----|
\ Meanwhile, tokenization works by replacing critical data with unique, non-sensitive tokens. These tokens have no intrinsic value or meaning and cannot be reverse-engineered without access to the secure tokenization system.
\
| import uuiddef tokenize(data): # Generate a token for the sensitive data return str(uuid.uuid4())sensitivedata = "1234567812345678"token = tokenize(sensitivedata)print(token) # Example Output: e3b0c442-98fc-4620-a923-4a2818f28290 | |----|
\ From the example above, you can see that the token is mapped securely to the original data in an encrypted database for retrieval only when necessary.
Fraud Prevention in FintechDue to constant changes in technology and the increase in the frequency of online transactions, most fintech start-ups are not always fully equipped to prevent fraud when they arise.
\ Emerging cyber threats like deepfakes, synthetic identities, and other AI-powered scams present significant challenges to these companies. Below are some new technologies I use and recommend to developers to tackle financial fraud.
Fraud Detection Technologies for Fintechs AppsI recommend incorporating AI/ML tools in fraud detection systems due to their effectiveness.
\ Machine learning algorithms can identify phishing patterns, suspicious links, or even automated scam messages using natural language processing (NLP) and behavioral cues.
\ Another advantage is that predictive AI models can assess risk scores in crypto transactions, and then provide fraud alerts once an anomaly or unusual pattern is detected. Most of the AI models that my company has developed are trained on historical data so that it can label transactions that meet certain criteria as legitimate and some others as illegitimate.
\ For example, if a user who typically makes small, regular purchases suddenly turns around to make a large withdrawal to a foreign account, this could be flagged as an anomaly by the model.
\ Again, based on the data input and the model’s predictions, each transaction or activity could be assigned a risk score. What this means is that transactions with scores above a certain threshold could be flagged for human review. Developers can also leverage blockchain technology in addition to the AI and ML tools. Blockchain provides a clear and immutable audit trail that simplifies compliance with anti-fraud regulations like KYC (Know Your Customer) and AML (Anti-Money Laundering).
\ Immutable records on blockchain also ensure that financial firms have a verifiable identity management system to prevent identity forgery.
\ I believe by building all these fraud-prevention features directly into the app architecture, businesses are better positioned to stand against advanced threats while maintaining user trust.
Security Challenges and Solutions in Mobile PaymentsMobile payments, while efficient, introduce several attack surfaces that can be exploited by threat actors.
\ From my experience, most vulnerabilities in mobile payment systems today can be traced down to the device level. Malware infections and the use of rooted or jailbroken devices can compromise sensitive data when they bypass built-in protections.
\ Another risk in mobile payment is in the network transmission channel itself. When there is leakage or vulnerability during data transmission, it can expose payment data to interception risks if not corrected quickly.
\ These risk factors remain a primary challenge to fintech app developers, but how can they be tackled?
\ While various solutions exist, I recommend secure SDKs and APIs for their effectiveness in guaranteeing mobile payment security.
\ These solutions are designed to enforce strong encryption and authentication protocols for payment apps. They ensure that all important data is encrypted using industry-standard protocols like Transport Layer Security (TLS)
\ Many secure SDKs and APIs are also pre-certified for compliance, so mobile payment systems can remain compliant with regulatory requirements with minimal effort. Implementing SDK and API is simple in just 3 steps:
System analysis and integrationThe first phase is to analyze the client's existing architecture and vulnerabilities so that proper SDK will be integrated. A custom API will also be added shortly, and the process can take up to two weeks.
Testing and optimizationThe next phase is where the QA team will conduct penetration testing to identify and fix potential weaknesses. API requests will also be optimized to ensure low latency for an uninterrupted user experience.
Deployment and trainingThe last stage is usually where my team deploys the solution with minimal downtime and conducts training sessions for the client's developers and security team on maintaining and scaling the new system.
\ Also, incorporating Secure Elements (SE) and Trusted Execution Environments (TEE) in payment apps can help isolate sensitive operations, as well as shield them from malware and tampered devices.
\ It is important to take your mobile payment app security issue seriously. If you can't do it yourself, it's better to outsource to the right candidates.
Securing Crypto WalletsCrypto wallets are used to store private keys needed to access and manage cryptocurrencies. The decentralized nature of cryptocurrencies means there is no central authority to turn to for recovery when there is a security breach in those wallets.
\ In fact, a single lapse in security such as compromised devices or stolen private keys can result in irreversible loss of crypto funds. Bugs in smart contracts may also expose funds to exploits.
\ Another factor that may lead to security breaches in crypto wallets is the custodian. Custodial wallets rely on third-party security to hold private keys, and there might be compromise if the wallet custodian goes bankrupt or gets hacked.
\ While non-custodial wallets put users in charge, they also heighten risks if keys are mishandled.
\
There are three ways in which individuals can securely store their crypto assets – hardware wallets, multi-signature wallets, and cold wallets.
\ Hardware wallets store private keys offline, and this makes them immune to hacking attempts or malware infections targeting online wallets. They often come with additional layers of protection, such as PIN codes and recovery phrases.
\ Multi-signature (multisig wallets) require multiple private keys to authorize a transaction. They are more popular in joint accounts and organizational treasuries, where they ensure consensus-based asset management.
\ Then there are Cold wallets, which are basically any cryptocurrency storage solution that remains completely offline. Cold wallets are nearly impervious to hacking attempts, phishing attacks, and ransomware.
\ That said, cryptocurrency traders need to know the importance of using a secure crypto wallet to avoid being exploited by cybercriminals.
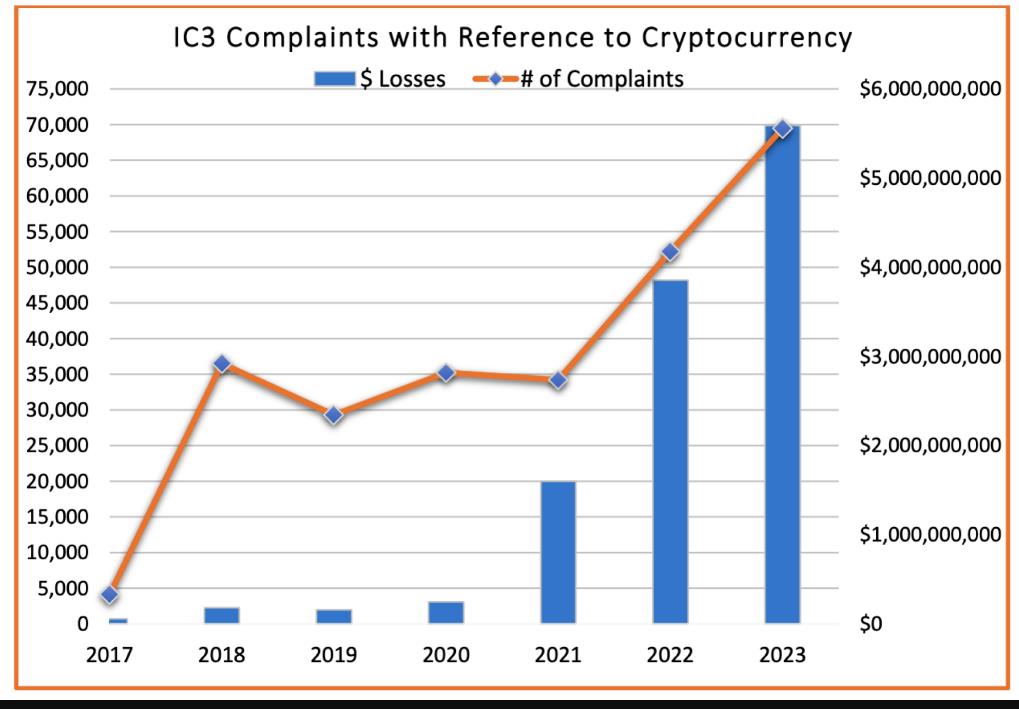
Crypto scams are steadily on the rise as revealed by the FBI graph shown in figure 5.
\ Software engineers building crypto apps should prioritize strong verification. Methods like biometric authentication and decentralized identity (DID), as implemented in our apps, provide a high level of protection against unauthorized access to crypto applications.
ConclusionCybersecurity is crucial for the survival of fintech firms today. The digital nature of their processes opens the door to cyberattacks, with new threats constantly cropping up.
\ As an experienced engineer in the software and IT industry, I urge businesses offering financial services, especially start-ups, to step up their security game.
\ Adopting best practices like data encryption, multi-factor authentication, and regular security check-ups can help fend off vulnerabilities. Cybercriminals aren’t sitting around, so neither should you.
\ The company, whose examples and techniques have been highlighted in this article, has worked with numerous businesses to iron out software development challenges, integrating secure coding and real-time monitoring into mobile app development.
\ A good case study for this service delivery involved helping a client increase operational efficiency and user trust using SDK and API dynamic risk assessment. This approach reduced manual intervention for suspicious activity by 70%, saving significant time for the client's operations team.
\ In the end, shoring up defenses and staying ahead of evolving threats means that fintech companies can not only protect user trust but also boost innovation without compromising safety.
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.