and the distribution of digital products.
DM Television
Understanding Sentinel: A Comprehensive Overview
- Built in the Cosmos ecosystem, Sentinel is mostly known as a dVPN application. However, it also provides a platform for application development using its zone/hub infrastructure and SDK toolkits.
- Following its protocol upgrade in September 2023, Sentinel observed a 1,339% increase in session counts QoQ, rising from an average of 357 to 4,780. This growth was driven by the implementation of onchain subscriptions and time-based payment options.
- On July 1, 2024, Sentinel announced an expansion to include an AI data layer, enhancing its capabilities to incorporate peer-to-peer marketplace functions and AI functionalities.
- Sentinel's infrastructure includes dVPN nodes in 408 cities across 110 countries.
- Sentinel Shield dVPN, launched in May 2024, is an open-source, decentralized app. It uses blockchain for peer discovery and connection authorization to ensure encrypted data handling.
Despite its many benefits, today’s internet faces significant threats from increasing censorship and invasive data collection, compromising fundamental human rights to privacy and information access. Traditional virtual private networks (VPNs) once offered secure access to geo-restricted content and increasing privacy. However, their effectiveness has diminished due to centralization, security breaches, and easily identifiable nodes.
The decentralized virtual private network (dVPN) model addresses these challenges. Sentinel, in particular, leverages the Cosmos ecosystem to create a decentralized, scalable, and cost-effective network. This system enables both individuals and organizations to develop private networking solutions with enhanced security and privacy. Sentinel helps existing VPN providers transition to decentralized architectures, deepening their trust with their user base and expanding their service capabilities.
BackgroundSentinel's inception and development into a decentralized VPN (dVPN) provider stemmed from a collective dissatisfaction with the centralized VPN model prevalent in the mid-2010s. Around 2017, a group of developers were inspired by decentralized technologies like the TOR network and peer-to-peer bandwidth sharing. They envisioned a new model that would facilitate a peer-to-peer bandwidth marketplace. This idea was catalyzed by the limitations observed in centralized VPN solutions, which often suffered from issues like a lack of privacy, potential data logging, and single points of failure.
Sentinel was founded by anonymous individuals, with a key developer known by the pseudonym “Tony Stark”. The team initially built their system on Ethereum, a popular choice at the time due to its widespread use and supportive developer community. However, they soon encountered the inherent limitations and tradeoffs associated with Ethereum’s design, particularly concerning scalability and transaction fees. These challenges were particularly highlighted by Ethereum's Proof-of-Work (PoW) consensus mechanism at the time.
The realization of these limitations led Sentinel to commit to transitioning to the Cosmos network in 2018. Cosmos offered several advantages crucial for Sentinel’s operational needs, including interoperability, faster block times, and increased throughput. This shift enabled the dVPN application to efficiently query the blockchain for real-time information about nodes offering bandwidth. As such, the system became more decentralized by eliminating reliance on any single company to host node information. Instead, data about the nodes was recorded on the blockchain and accessible via API, allowing for a more robust and trustless network.
Sentinel officially launched its native blockchain on the Cosmos network on March 27, 2021. The move to Cosmos not only addressed the issues of scalability and transaction speed but also allowed Sentinel to benefit from the network's community-driven ethos, which encourages collaboration among projects rather than competition. This environment was more conducive to the foundational principles of decentralization that Sentinel valued.
Following the announcement on July 1, 2024, Sentinel rebranded and expanded its vision to include an AI data layer. This move signaled a return to its original inspiration of a peer-to-peer marketplace that goes beyond just dVPN services.
In 2017, the SNT Foundation was one of leading organizations of Sentinel at the time. It successfully conducted a token sale, raising $2 million USD, which funded its operations for the following three years. During this period, the Foundation developed multiple dVPNs on the Ethereum platform, among which Sentinel dVPN emerged as the most notable. It achieved nearly 500,000 downloads before being discontinued in 2021 due to Sentinel's migration to the Cosmos network. It wasn't until 2020 that Sentinel managed to secure an additional $3.5 million through strategic funding rounds from venture capital firms focused on blockchain and technology, including Woodstock Fund, Atka, Genblock Capital, Zokyo, and Digital Strategies.
TechnologyVPNs vs. dVPNsAs we navigate the complexities of the digital age, the distinction between traditional VPNs and dVPNs becomes increasingly significant, especially within the crypto revolution that champions the ethos of decentralization.
Traditional VPNs: Centralized Privacy SolutionsVPNs serve as a pivotal tool for users seeking to enhance their online privacy, secure their internet activities, and bypass geographical restrictions. Operated by centralized entities, these services route user internet traffic through designated servers, effectively masking the user’s IP address and encrypting data to shield it from prying eyes. However, this centralization poses several risks. Such as users must trust the VPN provider to handle their data ethically. Despite assurances, there's no verifiable way to confirm that these providers don’t keep logs or share data with third parties. Also, centralized systems are susceptible to breaches. If a VPN provider’s server is compromised, all user data accessible through that server could be exposed. Lastly, the physical locations of VPN servers can limit users' ability to access specific geographical networks, and ongoing subscription costs can accumulate, regardless of actual usage.
dVPNs: A Paradigm Shift with SentineldVPNs like Sentinel offer a new approach to online privacy and security by addressing the limitations of traditional VPNs through decentralization. Instead of relying on a central authority, dVPNs use a peer-to-peer model where data is routed through multiple nodes managed by different individuals or entities. This reduces the risk of system breaches, as compromising one node does not affect the entire network. Sentinel's software is open source, allowing ongoing review and improvement by developers and security experts. This continuous scrutiny helps identify and fix vulnerabilities promptly, enhancing the network's overall security.
Sentinel Architecture OverviewSentinel is a decentralized protocol designed to support the development of applications, including VPN services. Initially, Sentinel aimed to decentralize the VPN industry by creating a framework that facilitates the development of independent dVPNs. This framework supports a backend architecture that enables current VPN establishments to transition towards a decentralized VPN industry.
Choice of EcosystemSentinel is part of the Cosmos ecosystem due to its interoperability and efficient design. The Cosmos Inter-Blockchain Communication (IBC) module and its consensus governance mechanism enable Sentinel to handle cross-chain payments that interact seamlessly with other Cosmos ecosystem entities. This setup allows Sentinel to run its own blockchain within the Cosmos network, called the "Sentinel Hub,” which is built on the Cosmos SDK.
Network Structure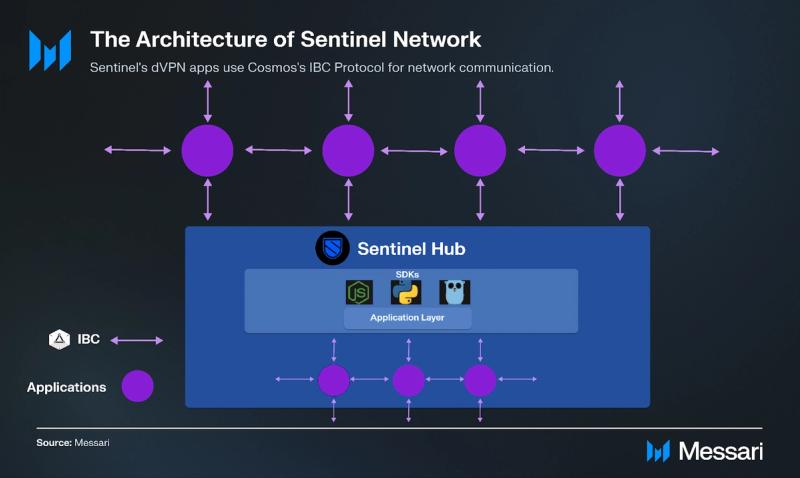
Sentinel leverages the Cosmos Hub/Zone architecture to efficiently scale its dVPN applications. The network can be constructed into two main components:
- Sentinel dVPN Zone (Sidechain): Manages application-specific transactions and data.
- Sentinel Hub (Main-chain): Handles generalized operations such as token transactions and governance.
dVPN applications can be built on either Sentinel's main chain or dedicated zones, depending on their throughput needs. Currently, the Sentinel hub manages the required throughput, so the hub/zone architecture hasn't been implemented. If transaction volumes increase significantly, zones will be established to support additional dVPN applications.
Tendermint Core and Consensus MechanismSentinel utilizes the Tendermint core through the Cosmos SDK for its blockchain framework. The Sentinel-Tendermint blockchain can host decentralized applications (dApps) or services that operate in their own independent zones, each with specific governance built on top of the Tendermint consensus, allowing their own set of validators to verify transactions.
Tendermint uses a bonded Proof-of-Stake (bPOS) consensus mechanism, allowing blockchains to establish a finite number of validators. This approach aims to achieve quick consensus, increasing overall throughput and transactions per second (TPS) while protecting the network from Byzantine faults. The bPOS mechanism achieves near-instant finality through a round-robin-based voting system, where tokenholders bond tokens to trusted validators. This is advantageous for marketplaces and privacy-focused applications like Sentinel, which require high privacy and handle a high volume of microtransactions.
GovernanceGovernance on Sentinel’s Cosmos-based mainnet is managed by validators, who are democratically selected through token delegation by network participants. The influence of these validators, referred to as "Voting Power," is determined by both the amount of tokens delegated to them and their historical performance. The governance structure allows for handling critical proposals such as the acceptance of new validators or zones, the rejection of malicious entities, and modifications to supply policies or account statuses without the need to fork to a new chain.
How does Sentinel dVPN work?Traditional centralized VPNs mask the user's IP address and encrypt data to protect against interception or tampering by ISPs and other entities. They reroute internet traffic and control connections between servers and nodes, creating single points of failure and attractive targets for hackers or government agencies. These VPNs optimize their servers to handle high traffic volumes, ensure low latency, and meet high throughput demands, especially with data-intensive activities like streaming.
In contrast, Sentinel dVPN uses a decentralized network with globally distributed nodes, improving security and reducing reliance on centralized points. These nodes can be desktop or laptop computers, mobile phones, or cloud servers, forming a robust, censorship-resistant system.
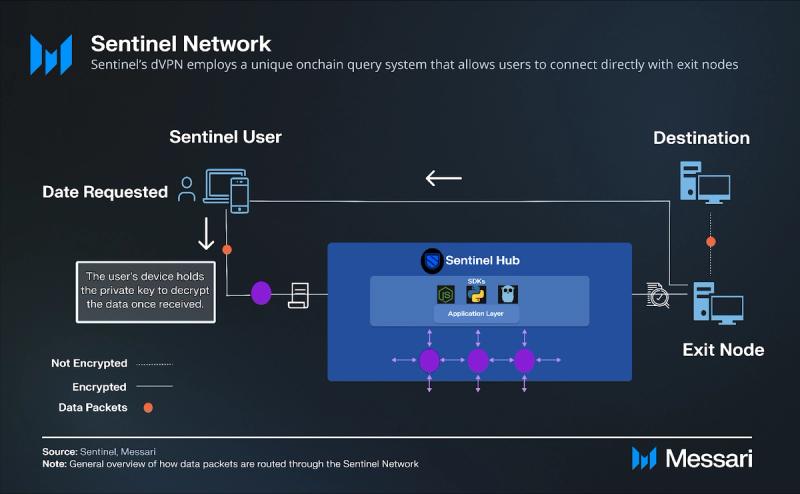
Sentinel’s dVPN employs a unique onchain query system that allows users to connect directly with exit nodes, bypassing intermediary servers. This system uses blockchain technology as a ledger for node querying. Nodes store and share their properties and connection instructions on the blockchain, and users generate a list of available nodes by querying this data from transactions on Sentinel’s dedicated dVPN zone. Authentication and identity are managed onchain, with potential failure points primarily at the consensus level. By contrast, traditional VPNs use centralized servers capable of logging interactions and revealing IP addresses.
When a user requests a connection on Sentinel’s dVPN, their application queries the blockchain to retrieve a list of available exit nodes. The user then selects a suitable node based on criteria such as latency and location. The user's device establishes a direct, encrypted tunnel to the chosen exit node, allowing data packets to be sent directly from the user's device to the exit node through this secure tunnel. This method avoids intermediary nodes, thereby minimizing the risk of data interception and ensuring that interactions remain strictly between the blockchain and the chosen exit node.
Smart contracts manage the registry of available dVPN nodes, keeping the information up-to-date via onchain queries. VPN session details and payments, made with the DVPN token, are recorded on the blockchain. The Sentinel dVPN is supported by a global network of validators and nodes, with account management, server querying, and network operations all handled onchain. This direct communication avoids logging or data compromise at intermediary points, reduces latency, and maintains the integrity of the user’s privacy.
Sentinel uses a Delegated Proof-of-stake (DPoS) mechanism via Tendermint, with 80+ validators selected by the community, scalable through governance mechanisms.
Sentinel's "proof-of-bandwidth" protocol transparently measures the bandwidth provided by nodes to end-users, establishing trust and determining service-level compliance to avoid penalties.
Sentinel employs Packet Normalization to ensure that the size of every request and response is almost identical, which prevents data sniffing. A core feature of Sentinel’s dVPN service is its no-logs policy, which ensures that the network does not store any identifying information about user activities. The decentralized nature of the network ensures that no single node has complete information about user activities or data paths. Sentinel supports this claim with cryptographic proofs that validate the no-logs policy, demonstrating compliance without relying on manual audits.
Sentinel Network Nodes: dVPN and Validator NodesIn the Sentinel network, nodes are categorized into two main types: validator nodes and dVPN nodes.
1. dVPN Node - Exit nodes: Can be set up using a Virtual Private Server (VPS), a local Raspberry Pi, or the Akash Network, so long as the user meets the hardware specifications.
Hardware Specifications:
- CPU: Multi-core (2+ cores)
- RAM: Minimum of 4 GB, preferably 8 GB
- Storage: 40-100 GB SSD
- Bandwidth: Minimum 10 Mbps, recommended 100 Mbps for high traffic
- OS: Linux, especially Debian or Ubuntu 20.04 LTS
- Public IP: Static preferred
- Security: Firewall and port forwarding, regular updates and backups
2. Full Node and Validator Node: Operating as a Sentinel Validator involves setting up a full node and initiating a validator transaction. This setup can be implemented on various platforms, including dedicated servers, home systems, or through the Akash Network, so long as the user meets the hardware specifications.
Hardware Specifications:
- CPU: High-performance like Intel Xeon E3-1220 V2 or better for full nodes; validator nodes require more robust CPUs (8+ cores)
- RAM: 32 GB for full nodes; validator nodes need 16 GB or more
- Storage: 1-2 TB SSD in RAID for full nodes; 500 GB or more for validator nodes
- Bandwidth: Unmetered at 1 Gbps, with higher requirements for validator nodes (50 Mbps or more)
- Network: Low-latency, stable Ethernet connection with open ports specific to node type (e.g., 26656 and 26657 for validator)
- Security: Robust security measures including DDoS protection, firewall rules, and security updates
Sentinel integrates V2Ray's versatile networking capabilities to enhance its decentralized VPN service, ensuring secure and adaptable communication across different network environments.
V2Ray, developed as part of Project V to help users build private networks over the internet. It can function alone or with other tools, making it adaptable to different network environments. V2Ray supports multiple protocols, including Socks, HTTP, Shadowsocks, and VMess, with customizable routing and obfuscation to bypass censorship and ensure secure, anonymous communication. Additionally, V2Ray can handle complex network configurations and offers a platform for developers to create or integrate proxy solutions. It features multiple inbound/outbound proxies, customizable routing, and reverse proxy support, and is compatible with Windows, Mac, Linux, and mobile devices.
Sentinel dVPN and V2Ray's Camouflage CapabilitiesSentinel dVPN leverages V2Ray’s camouflage capabilities, often referred to as "obfuscation," which are designed to disguise the traffic generated by its protocols. Doing so prevents detection and interference by third parties, such as internet service providers or governmental censors. Some of the key techniques used include TLS obfuscation, multiple transport protocols, domain fronting, and customizable routing.
These features make V2Ray a useful tool for maintaining privacy and access in environments with restrictive internet censorship. They could help Sentinel eventually bypass “The Great Firewall of China.” As one of the first DePIN projects in China, Sentinel dVPN uses a secure proxy protocol called SOCKS5. SOCKS5 employs SSH and RSA-based encryption protocols to securely transfer data with authentication over a proxy server. Sentinel also uses HTTPS/TLS to package traffic through the firewall.
HTTPS/TLS ObfuscationHTTPS and TLS are secure versions of HTTPS, the protocol used for transferring data over the web. HTTPS includes encryption through TLS (Transport Layer Security) or its predecessor SSL (Secure Sockets Layer). This encryption secures the data from eavesdroppers and is standard practice for protecting sensitive transactions.
The process involves wrapping or tunneling the actual data transmitted (which could be blocked by a firewall) within HTTPS/TLS traffic. Since HTTPS is widely used for secure communications on the internet, many firewalls are configured to allow HTTPS traffic through by default.
By using HTTPS/TLS, the real nature of the traffic is hidden, which is useful in heavily censored or monitored environments. Tools like VPNs and certain proxy servers use similar techniques to disguise their traffic. When VPNs, use this method, a form of obfuscation, it makes the data look like typical HTTPS traffic, allowing users to access blocked resources or maintain privacy without drawing attention. This approach reduces the likelihood of V2Ray nodes being blocked or interfered with, ensuring a stable internet experience.
TokenomicsThe DVPN utility token serves multiple roles in governance, staking, payment, and revenue sharing:
- Governance: DVPN tokenholders vote on network upgrades, protocol changes, and fund allocation, enabling a decentralized, community-driven evolution of the network.
- Staking/Work Token: Tokenholders stake DVPN tokens to participate in network security and consensus mechanisms, earning rewards from node operations. Validators and delegators secure the network by staking tokens, with validators proposing and validating blocks.
- Payment for Bandwidth: DVPN tokens are used to purchase bandwidth from network node hosts, facilitating access to dVPN services. Payment options include:
- Pay-as-you-go and Escrow Payments: Direct payment for the desired amount of bandwidth. DVPN tokens are staked in escrow for advanced services, managing real-time payments based on bandwidth consumption, supporting pay-per-GB or subscription models.
- Periodic Subscription: Recurring fees paid in fiat or other currencies, converted to DVPN tokens for node hosts.
- Revenue Sharing: Node owners share 20% of their earnings with DVPN stakers, directly linking rewards to network usage and success.
Transaction Fees: Users pay fees in DVPN for actions such as transferring tokens or executing contracts. These fees are collected by validators to compensate contributors to network operations.
Tokenomics OverviewSentinel transitioned from an initial Ethereum-based supply of 2 billion (SENT) tokens to a Cosmos-based supply of 10 billion (DVPN) tokens. The maximum supply is capped at 48 billion tokens.
Sentinel employs a structured inflation model:
Period 1: DVPN’s inflation rate was divided into 6-month epochs. The initial inflation rate at genesis will be 49% (monthly rate of 4.0833%) and decreased by 6% after each epoch until reaching a 13% annualized inflation.
Period 2: An exponentially decaying emission curve, similar to the Akash Network, reduces inflation to approach zero as the maximum token cap of 48 billion is reached.
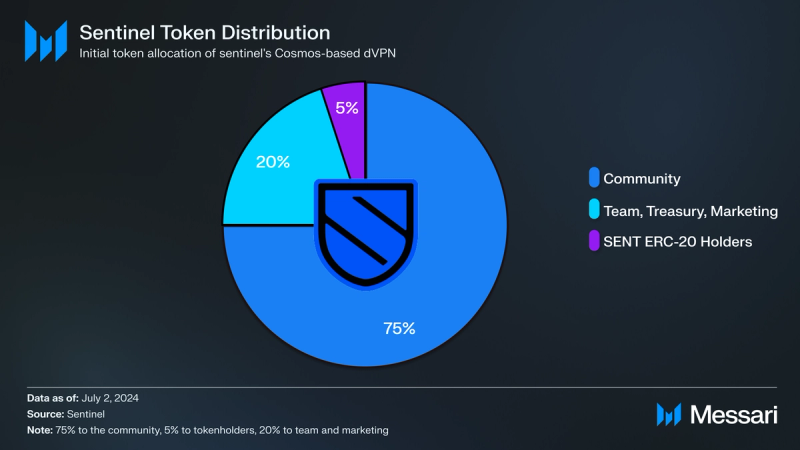 Distribution Buckets and Lock-ups:
Distribution Buckets and Lock-ups:- Community: 75% of the token supply was allocated to the community in the Ethereum-based model. This allocation continues as the network transitions to Cosmos’ initial supply to ensure community involvement and decentralization.
- SENT ERC-20 Tokenholders: 5% of the initial token supply. Holders received a bonus of 400 million Cosmos-based tokens upon conducting the swap and staking their tokens for a minimum of 12 consecutive months. The bonus had a 12-month cliff and was distributed over a period of 12 months vested which ended in March 2022.
- Team, Treasury, and Marketing: 20% of the initial supply was set aside to fund development, operational expenses, and marketing efforts. The lock-up schedule is designed with a distribution heavily weighted towards later years:
- Year 1: 0%
- Year 2: 12%
- Year 3: 30%
- Year 4: 60%
- Year 5: 100%
Locked tokens can be staked to earn various rewards. These rewards encompass liquid returns from network inflation and transaction fees, as well as revenue sharing from dVPN node hosts. Importantly, any rewards earned on staked and locked tokens are also subject to the same vesting and lock-up conditions as the principal tokens. This ensures network stability by preventing immediate sell pressure.
Validators and Fees:
- Maximum Validators: Starts with 50 validators and is scalable through governance. There is a minimum validator fee set at 0.25% to prevent unfair advantages at the start of the network.
- Unbonding Time: 28 days for unstaking tokens.
- Node Host Subsidies: The community pool takes 2% of block rewards for incentives.
Revenue Sharing and Node Incentives:
- Revenue Sharing: 20% of earnings from dVPN node owners are distributed to DVPN stakers.
- Payment Flexibility: dVPN node hosts can accept various tokens post-IBC (Inter-Blockchain Communication) integration.
Foundation Delegations:
Foundation Support: Delegates to validators with a commission cap of 5%.
Protocol UsageNetwork Activity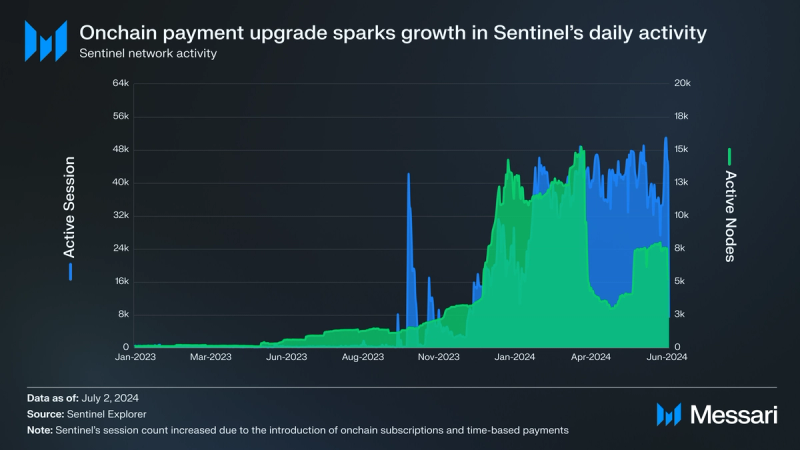
After its protocol upgrade in September 2023, Sentinel’s session count increased due to the introduction of onchain subscriptions and time-based payments. The average session count rose from 357 to 4,780 from June to November 2023, resulting in a 1,339% increase QoQ. Previously, Sentinel facilitated peer-to-peer transactions where community-hosted dVPN nodes priced their bandwidth services per GB. The upgrade allowed nodes to set monthly rates (or any custom time period) for unmetered bandwidth usage. Following the upgrade, dVPN applications could aggregate nodes, lock tokens with them to create subscription plans, and offer unlimited access at a flat monthly rate. This model is similar to centralized VPNs where users pre-pay for bandwidth and applications resell it.
Before the upgrade, subscribing to individual nodes was time-consuming, taking up to a minute per node. After the upgrade, nodes could set prices based on service hours, with tokens locked and deducted hourly based on node uptime, verified onchain. This standardization simplified pricing and allowed better management of profit structures and infrastructure costs.
The upgrade consolidated prices in the node market but required new service-level agreement monitoring. It became crucial for white-label applications to ensure nodes have adequate technical specifications to handle multiple sessions in order to incorporate them into digital subscriptions confidently.
EcosystemSentinel Networking and Marketplace ProtocolThe Sentinel networking and marketplace protocol is designed to facilitate seamless peer-to-peer interactions between bandwidth providers (supply side) and bandwidth/VPN consumers (demand side).
Demand Side Participants:
- Individual Users.
- Enterprise Businesses/Website or Mobile Application Operators.
- Centralized VPN Service Providers.
Supply Side Participants
- dVPN Node Hosts.
- Retail/Individuals.
- Data Centers/Professional Node Service Providers.
- Centralized VPN Providers: Traditional VPN companies that supply bandwidth to the Sentinel network, integrating decentralized options into their service offerings.
- dVPN Application Creators.
The Sentinel Network boasts a robust infrastructure with dVPN nodes spread across 408 cities in 110 countries. The top ten countries by node count are the United States (1,731 nodes), Germany (570 nodes), Malaysia (544 nodes), United Kingdom (259 nodes), The Netherlands (251 nodes), Singapore (201 nodes), Australia (107 nodes), Finland (103 nodes), Indonesia (78 nodes), and Spain (76 nodes). In addition to these nodes, the network features 883 Handshake resolvers.
The DVPN token is available on both centralized and decentralized exchanges:
Centralized Exchanges (CEX)
Decentralized Exchanges (DEX)
 Ecosystem and Peers
Ecosystem and PeersSentinel leverages the interoperability of the Cosmos ecosystem, partnering with notable protocols such as Osmosis, Akash, Axelar, Juno, and Cosmos Hub.
Whitelabel dVPN SolutionsSentinel's primary focus includes several whitelabel dVPN solutions that are currently live:
- Sentinel Shield dVPN: Launched in May 2024, Sentinel Shield dVPN is a decentralized DePin consumer application with an open-source, peer-to-peer architecture. It uses blockchain technology for peer discovery and connection authorization, ensuring encrypted and safe data handling. Powered by V2Ray and WireGuard, it is available for Android devices.
- Nors VPN: The Nors VPN Quick Client, formerly Solar dVPN, and the dVPN Bot, a Telegram mini-app, work together to provide access to Sentinel's decentralized VPN nodes. The Nors VPN Quick Client supports Wireguard and V2Ray configurations and is available for iOS, Mac, and Android. Users start by accessing the dVPN Bot on Telegram, where they can select a server from over 8,000 community-hosted options and receive access credentials. These credentials are then used with the Nors VPN Quick Client to establish secure and encrypted connections. The bot also creates a Sentinel wallet and enrolls the user in an onchain subscription plan, granting access to the Telegram Mini-App. This collaboration aims to expand the Sentinel dVPN ecosystem, leverage the reach of Telegram, and gather feedback to develop a monetized product supporting TON payments, backed by the TON Foundation.
- Meile dVPN: Meile dVPN creates a private, censorship-resistant network using blockchain technology and community-hosted nodes. It introduces a fiat gateway for decentralized VPN access, allowing credit card payments through Stripe, with DVPN tokens sent to the Meile Wallet. It is also available as a desktop client on Linux and Mac.
- V2App: V2App transitioned from a centralized to a decentralized VPN, powered by the V2Ray platform. Focused on privacy, security, speed, and reliability, it moved to Sentinel in 2024. Known for its V2Ray protocol, it is now a fully decentralized VPN application.
- Breadcrumbs dVPN: Breadcrumbs dVPN enhances security by protecting users' digital footprints and rewarding them for their data, ensuring a secure browsing experience.
- Dogwifhat dVPN: A memecoin-themed application within the Sentinel ecosystem, Dogwifhat dVPN is open-source and provides a secure decentralized VPN service.
- Bagimsiz VPN/Independent VPN: Operating in Turkey, Independent VPN helps users bypass internet censorship and protect their connection. It is powered by WireGuard and V2Ray.
- Decentr Browser: Decentr Browser integrates Sentinel dVPN and Adblock for enhanced speed, security, and utility. It is a Web3 browser based on Cosmos but chain-agnostic, allowing users to generate Personal Data Value (PDV) and earn DEC coins. It includes DeFi features, dVPN, Adblock, a publishing portal, and AI chat, all payable by DEC. Desktop versions are available for Windows, Mac, and Linux with built-in Sentinel dVPN.
Sentinel is focused on expanding its user base and developing a decentralized VPN industry. It aims to help institutional VPNs transition to decentralized infrastructure and provides comprehensive toolkits for developers. Three whitelabel SDKs are currently available: Golang, JavaScript, and Python.
Recent Milestones- Sentinel Shield App Beta Launch (APK): A security-focused dVPN application designed for mobile users.
- Airdrop dVPN Update: The Airdrop dVPN, now live for testing, will implement a permissioned access structure to address concerns from node operators and developers regarding subscription management.
- Sentinel DePIN Hardware: Raspberry Pi Sentinel dVPN Node Hosting allows users to set up and monetize their own dVPN nodes using Raspberry Pi devices. Sentinel dVPN is integrating with Open-WRT-based routers, allowing router owners to monetize their bandwidth by becoming node hosts. This setup provides dVPN access across the entire Wi-Fi network, removing the need for individual VPN installations on each device. Users can also create a secondary network dedicated to dVPN access. This integration is cost-effective for participants in developed economies with reliable internet connections.
- BTC dVPN and XMR dVPN: New white label applications targeting Bitcoin and Monero users, providing specialized VPN services.
- ATOM dVPN: Design work is complete, with plans to launch on iOS and Android, catering to ATOM users.
- New Websites: New Sentinel websites for hardware and residential nodes are in development, following successful tests of Raspberry Pi-based hardware nodes announced in December.
These initiatives and tools improve Sentinel’s network capabilities, broaden its user base, and provide developers with the resources to build on the Sentinel network, supporting growth in the decentralized VPN industry.
Sentinel Growth Highlights- On February 22, 2024, Sentinel announced its partnership with Dragon VPN to introduce Dragon dVPN in China, aiming to expand decentralized VPN usage to over 1 billion internet users. This collaboration, funded by the Sentinel Growth DAO, will integrate with popular Chinese payment platforms like WeChat and Alipay, making VPN services accessible and user-friendly. Additionally, USDT crypto payments will be supported.
- On January 12, 2024, Sentinel successfully implemented an additional IBC relayer, enhancing infrastructure to ensure more reliable trading and addressing previous limitations caused by relying on a single relayer.
- The largest announcement on July 1, 2024, introduced Sentinel's new AI data layer and peer-to-peer bandwidth marketplace for Web3, marking a significant shift from a dVPN network to a global bandwidth marketplace. This evolution includes using mobile phone IP addresses for data scraping and leveraging the onchain Distributed Hash Table (DHT) for peer communication, positioning Sentinel as a key player in the AI data layer for Web3. Both the Sentinel dVPN Service and the Sentinel AI Data Layer facilitate data retrieval, yet their operational methods differ. The Sentinel dVPN Service allows users to connect in real time to a provider or exit node. Through this connection, data is securely requested via an encrypted tunnel from selected websites or servers, and payments for the services are generally calculated per unit of time. On the other hand, the Sentinel AI Data Layer also retrieves data from websites but operates under a different framework. It does not require immediate data download; instead, the data can be stored in decentralized caches, such as Jackal or IPFS. This allows users to access data without needing a continuous connection, providing the flexibility of offline access. Payments for this service are usually based on the amount of bandwidth used and the number of unique IPs involved.
- Sentinel has also launched a native blockchain explorer, developed with Interbloc, enhancing transparency and consolidating important data. This new explorer addresses the limitations of third-party options like Mintscan, promoting Sentinel's identity as a sovereign Layer-1 blockchain and ecosystem.
Sentinel offers a decentralized VPN (dVPN) solution that addresses the limitations of traditional, centralized VPNs by using blockchain technology and a peer-to-peer network. This decentralized approach enhances security and privacy by distributing network traffic across globally dispersed nodes. Built on the Cosmos network, Sentinel benefits from scalability and interoperability, utilizing features like proof-of-bandwidth and V2Ray's camouflage capabilities for enhanced security. The DVPN token is integral to Sentinel's ecosystem, as it facilitates governance, staking, and payment for bandwidth. Sentinel continues to expand its network and services, integrating with various platforms and offering white label solutions, while also focusing on future developments like an AI data layer and a peer-to-peer bandwidth marketplace.
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.