and the distribution of digital products.
DM Television
New Standard Addresses Shortcomings of JSON Web Tokens
PASETO (Platform-Agnostic Security Tokens) is a new standard for creating secure, stateless tokens, widely used in authentication and authorization. Built to address the shortcomings of JSON Web Tokens (JWT), PASETO prioritizes security, simplicity, and ease of use, making it an excellent choice for modern applications.
\ JWT tokens come with challenges, especially in cryptographic configuration, where flexibility can sometimes lead to vulnerabilities. PASETO eliminates this risk by enforcing the use of strong, predefined cryptographic algorithms. This ensures security without requiring developers to make complex cryptographic decisions. This design minimizes the chance of errors by providing a safer alternative to JWT
\ Another advantage of PASETO is its straightforward implementation. Developers don’t need to go through endless cryptographic options or worry about choosing the wrong algorithm. Each PASETO version comes with a carefully selected set of secure cryptographic tools, making it easier to integrate while maintaining high security standards.
\ Whether you are securing user sessions, transmitting sensitive data, or building scalable authentication systems, PASETO offers a modern, developer-friendly solution. By addressing the complexities and vulnerabilities of older token standards, PASETO has set a new benchmark for secure token-based communication
Structure of PASETO tokenPASETO token consists of three or four parts. Each part is separated by “.“ Below is the structure of PASETO token.
\
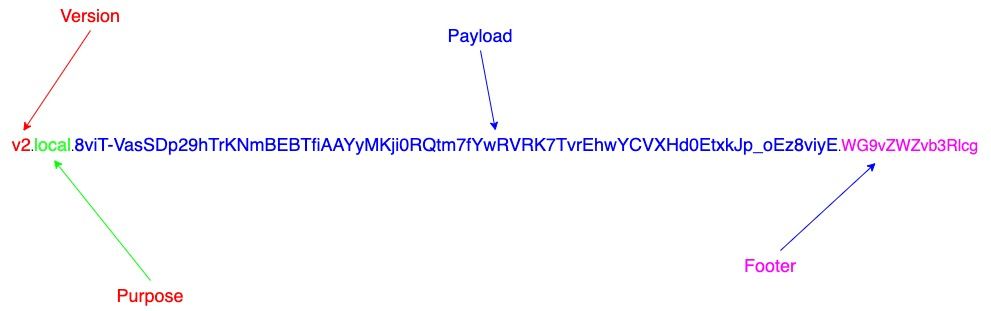
Version: This indicates the protocol version used to generate the token.
Purpose: There are two options here. Local (In this case, the token will be encrypted) and Public (In this case, the token will be signed). Payload: This contains the Claims and Data. For the local tokens, the payload is encrypted with a secret key and base64 encoded. For public tokens, the payload is in plain text and base64 encoded.
Footer: This is an optional section. And contains non sensitive information.
VersionPASETO comes in multiple versions. Developers don't need to go through endless cryptographic options or worry about choosing the wrong algorithms. Each PASETO version designed with specific cryptographic standards and use cases in mind. The version determines the cryptographic algorithms used and defines how tokens are generated and verified. As of today, there are 4 versions of PASETO available
\ Version 1: This is designed for legacy applications that needs to maintain both old and new security standards
Version 2: This is desinged for modern secure cryptographic standards
Version 3: This is designed for National Institute of Standards and Technology standards.
Version 4: This combines the strength of both V2 and V3
Purpose- Local
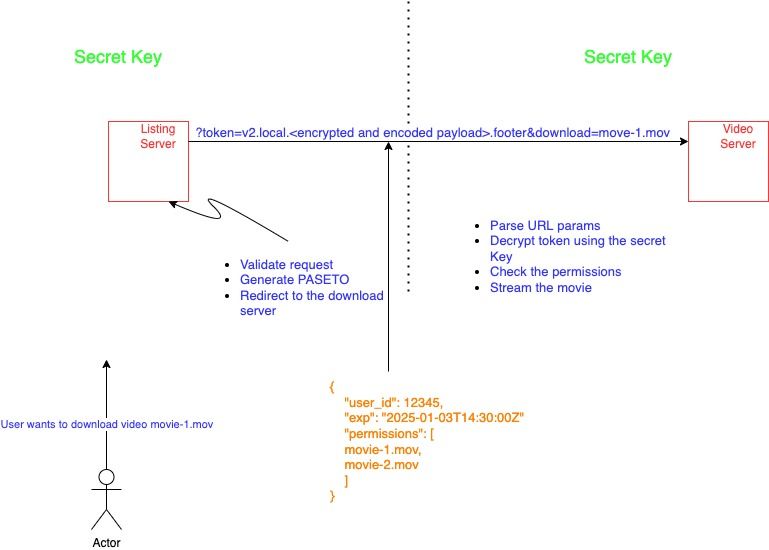
\ Local PASETO tokens are secure and encrypted. It uses symmetric encryption algorithm to protect sensitive information. This symmetric encryption ensures that the data within the token remains confidential and cannot be accessed by unauthorized parties. Only entities possessing the shared secret key can decrypt the token and retrieve the payload. See the diagram below to understand the interaction in case of PASETO ‘local‘ .
\ Example Token generation code for ‘local‘ PASETO token.
\
from pyseto import PasetoV2 from pyseto.exceptions import PasetoError import os # Function to create a v2 local PASETO token def create_v2_local_paseto(secret_key: bytes, payload: dict) -> str: """ Create a v2 local PASETO token. Args: secret_key (bytes): A 32-byte key for encryption. payload (dict): The data to include in the token. Returns: str: The generated PASETO token. """ # Initialize PASETO v2 with local purpose token = PasetoV2() try: # Encrypt the payload to create a local token paseto_token = token.encrypt(secret_key, payload, footer=b"optional-footer") return paseto_token except PasetoError as e: raise ValueError(f"Error generating PASETO token: {e}") # Example usage if __name__ == "__main__": # Generate a random 32-byte key (use a secure key in production) secret_key = os.urandom(32) # Define the payload (data) for the token payload = { "user_id": 12345, "username": "example_user", "exp": "2025-12-31T23:59:59Z" } # Create the token try: token = create_v2_local_paseto(secret_key, payload) print("Generated PASETO Token:", token) except ValueError as error: print("Error:", error)\
- Public
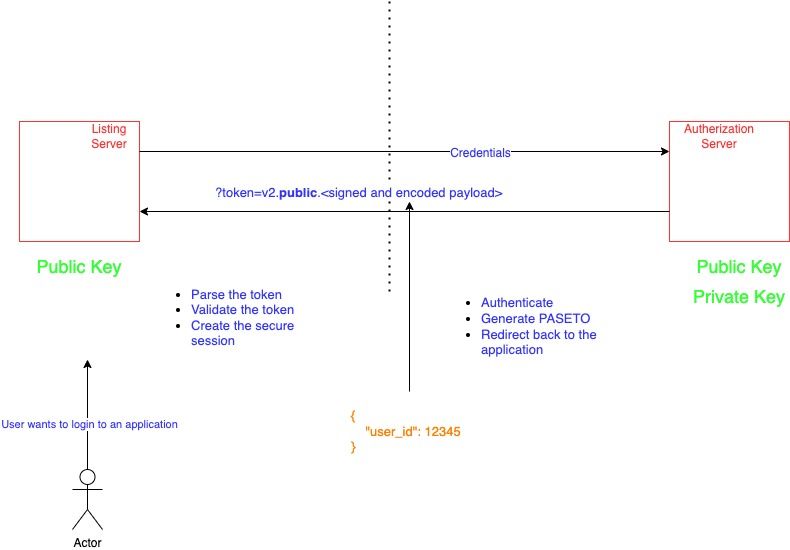
\ Public PASETO tokens are cryptographically signed using an asymmetric key pair, consisting of a private key (used to sign the token) and a public key (used to verify its authenticity). Unlike local PASETO tokens, public tokens do not encrypt their payload, meaning the data is visible to anyone who has access to the token. However, the signature ensures the integrity and authenticity of the data, making public PASETO tokens highly secure against tampering. See the diagram below to understand the interaction in case of PASETO ‘public‘
\
\ Example Token generation code for ‘public‘ PASETO token.
\
from pyseto import PasetoV2 from pyseto.keys import AsymmetricKey from pyseto.exceptions import PasetoError def create_v2_public_paseto(private_key: AsymmetricKey, payload: dict) -> str: """ Create a v2 public PASETO token. Args: private_key (AsymmetricKey): The private key for signing the token. payload (dict): The data to include in the token. Returns: str: The generated PASETO token. """ # Initialize PASETO v2 with public purpose token = PasetoV2() try: # Sign the payload to create a public token paseto_token = token.sign(private_key, payload, footer=b"optional-footer") return paseto_token except PasetoError as e: raise ValueError(f"Error generating PASETO token: {e}") # Example usage if __name__ == "__main__": # Generate a key pair (private and public keys) private_key = AsymmetricKey.generate() public_key = private_key.public_key() # Define the payload (data) for the token payload = { "user_id": 12345, "username": "example_user", "exp": "2025-12-31T23:59:59Z" } # Create the token try: token = create_v2_public_paseto(private_key, payload) print("Generated PASETO Token:", token) # Optional: Display the public key (use it to verify the token) print("Public Key:", public_key.encode().decode()) except ValueError as error: print("Error:", error)\
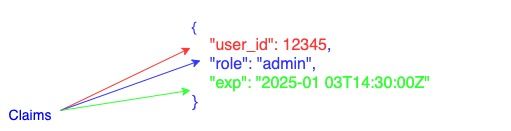
PASETO PayloadPASETO payload contains Claims. Each JSON key is a claim in PASETO. There are some reserved Claim keys. Please refer to the PASETO official documentation to know more on this.
\ Below is the decoded and decrypted payload from this PASETO token
v2.local.8viT-VasSDp29hTrKNmBEBTfiAAYyMKji0RQtm7fYwRVRK7TvrEhwYCVXHd0EtxkJp_oEz8viyE.WG9vZWZvb3Rlcg\
Footer is an optional component in PASETO token. It contains a base64 encoded string. It can contain meta data information that is not part of the Payload.
Use Cases of PASETO- Stateful server-side sessions using the local token
- Stateless authentication with public-key cryptography
- For secure inter-service communication where confidentiality and integrity are critical.
- As a secure alternative to JWT for issuing access and refresh tokens.
- For encrypted communication in client-server or peer-to-peer systems
- Scenarios where you need strict control over encryption and signing without risking insecure configurations.
PASETO tokens are not re-usable. If you have an application which needs to re-use the tokens, PASETO is not for you.
SummaryPASETO is an excellent choice for new projects prioritizing security and simplicity in token handling. Built on strong cryptographic foundations, PASETO mitigates common vulnerabilities such as algorithm confusion and insecure token formats, promoting better key management practices and ensuring robust protection. It offers two different types of tokens to suit various architectural needs: local tokens, ideal for stateful server-side sessions in traditional web applications, and public tokens, designed for stateless environments like micro services and API-driven architectures. With its focus on security, ease of use, and well-defined use cases, PASETO is a reliable standard for projects requiring high-security measures and standardized token solutions.
Referenceshttps://developer.okta.com/blog/2019/10/17/a-thorough-introduction-to-paseto#what-is-paseto
https://medium.com/@teal33t/breaking-down-paseto-vs-jwt-which-token-is-right-for-you-f084ed952586
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.