and the distribution of digital products.
Anonymous vs “ICE Air:” GlobaIX Needs A Security Fix
It seems that the suspension of TeleMessage’s services in the aftermath of “SignalGate” isn’t the end of cybersecurity troubles for Trump’s administration. The hacker group “Anonymous” hit GlobalX, also known as “ICE Air,” and leaked sensitive deportation flight files to the press.
\ GlobalX is the US charter service used by the US Immigration and Customs Enforcement Agency (ICE) for deportation flights. According to the hackers involved, this government-contractual airline was attacked on multiple cyber fronts.
\ The GlobalX developer’s token was discovered and used as a data breach point. “Anonymous” got in possession of security keys for the company’s AWS (Amazon Web Services) cloud storage that allowed them to exploit the whole digital infrastructure. The hackers’ focus was on flight logs, passenger lists, and itinerary details confirmed as authentic by the press.
\ “That stolen data, it turns out, included detailed passenger lists for GlobalX’s deportation flights—including the flight to El Salvador of Ricardo Prada Vásquez, a Venezuelan man whose whereabouts had become a mystery to even his own family as they sought answers from the US government. US authorities had previously declined to tell his family or reporters where he had been sent—only that he had been deported—and his name was even excluded from a list of deportees leaked to CBS News.”
\ “Anonymous” didn’t stop there. There are claims about internal messages sent to pilots by using NAVBLUE, an Airbus flight operations tool. In addition, GlobalX’s GitHub repository was compromised. The cherry on top was a defacement of one of the company’s subdomains with the well-known Guy Fawkes mask in the colors of the American flag.
\
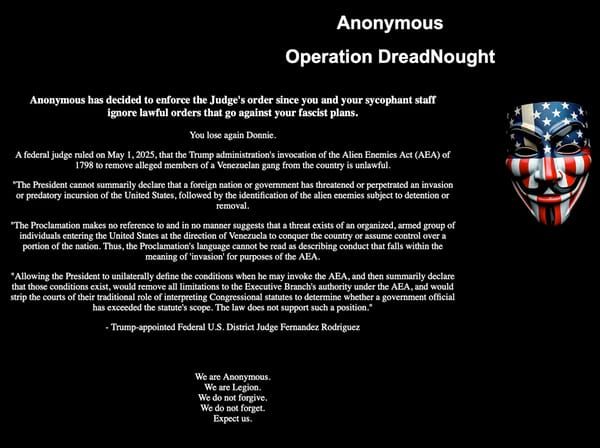
\ “Upon learning of this activity, the Company immediately (1) activated its incident response protocols and third-party cybersecurity experts to assist with containment and mitigation activities and to investigate the nature and scope of the incident and (2) took actions to contain and isolate the affected servers and prevent further intrusion,” [GlobalX said] (https://“Upon learning of this activity, the Company immediately (1) activated its incident response protocols and third-party cybersecurity experts to assist with containment and mitigation activities and to investigate the nature and scope of the incident and (2) took actions to contain and isolate the affected servers and prevent further intrusion,” GlobalX said.
\ “Although the Company is unable to predict the full impact of this incident, the Company does not expect the incident will have a material effect on the Company, or its financial condition or results of operations,). “Although the Company is unable to predict the full impact of this incident, the Company does not expect the incident will have a material effect on the Company, or its financial condition or results of operations.” \n
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.